// >> General
Using Javascript to Graph Sparklines
Deron Grzetich | 7. April, 2009
Graphing sparklines may appeal to those who have read the Edward Tufte books (I’m looking at you AJR) on the visual representation of data. On his blog he talks about sparklines here. If you consider yourself part of this group there is a pre-written Javascript sparkline generator you may be interested in by the name of jquery sparklines.
To set this up you’ll need: 1. Some data to graph, 2. A webserver where you can host the js and html files, 3. jquery and jquery.sparklines, 4. Some basic Javascript skills…maybe PHP or Phython if you plan on generating dynamic content for the lines.
Disclaimer: I used the graphs and data directly from the sparklines site because I’m too lazy to create my own numbers. Note that I’m limited in this post as I can’t use var or span id tag in a post, so these example all have inline static data. For an example of one using dynamic data see this page.
Example Sparklines:
Inline Sparkline: 1,4,4,7,5,9,10
Bar charts negative values:
Composite inline 8,4,0,0,0,0,1,4,4,10,10,10,10,0,0,0,4,6,5,9,10
Dow 90,10,25,150,180
Chances that Art will think sparklines bring any value
Microsoft Windows Update errors…0xC80003FB and 0xC80003FA
Deron Grzetich | 4. April, 2009
So I realize this isn’t exactly security related, but I felt compelled to post since it relates to errors with the Windows Update service. I recently dusted off some old virtual machines which were running Windows Server 2003 and when attempting to update via WU I encountered error 0xC80003FB and 0xC80003FA. These errors do not quite explain what your potential issues may be and in searching for the answer I came across some posts which actually worked and others which left me scratching my head. If you encounter this error, here are a few things to try:
View the contents of your Windows Update log file to see what it is complaining about. This file is located in %windir%/WindowsUpdate.log. The last few lines will show your most recent attempt at running WU. If you see the following lines:
WSUS server: http://name ofyourinternalWSUSserver
WSUS status server: http://name ofyourinternalWSUSserver
Target group: (name of the group this system was in…may be Unassigned Computers)
Windows Update access disabled: No
Then your system was trying to connect to WSUS. What I found interesting is that I had allowed this system to go out to the internet for updates as part of the WSUS options, yet it failed. Ask yourself if you added this machine to a WSUS installation and then deleted WSUS. I was testing WSUS at some point in the past and had pointed this system to the WSUS server for updates which is not longer part of my test environment. Here are some steps you can try that worked for me:
Stop the Windows Update service by going to Start->Run->service.msc
Backup, then delete, the registry key located at HKLM/SOFTWARE/Policies/windows/windowsUpdate (you’ll notice this has the WSUS server info you may have entered at some point in the past)
Restart the Windows Update service and go Windows Update
If this doesn’t work continue on to the next steps (I have a bad habit of trying many things at once when troubleshooting)
Stop the WU service again. Go to %windir%\SoftwareDistribution and find the DataStore directory. Delete the .edb file and Logs directory from this folder and restart the WU service. Try to connect to WU. If this doesn’t work, you can stop the WU service, rename the Software Distribution folder to something else, restart the WU service and again run Windows Update. This will rebuild that entire directory and should remove any corruption you had in these files that was causing an issue. In the end, a combination of removing the reg key and deleting the database worked to get updates flowing again. Hope this help.
Conficker Scanning Using NMap
Art Chaisiriwatanasai | 30. March, 2009
According to a post by the ISC and Skull Security tonight, its possible to scan for Conficker-infected hosts using something as simple as Nmap. All you need is the latest BETA version 5 of Nmap 4.85 and run it with the following flags:
nmap –script=smb-check-vulns –script-args=safe=1 -p445 -d <target>
Source:
http://www.skullsecurity.org/blog/?p=209
http://isc.sans.org/diary.html?storyid=6097
Safely Navigating Through the Internet Slums
Art Chaisiriwatanasai | 29. March, 2009
With all the Conficker (over)hype in the news lately, I thought it would be relevant to blog about a few ways to traverse some of the less than reputable parts of the Internet without messing up your computer. In our line of work, visiting sites that end in .ru and .cn are all too common. You all saw Hostel…you know what happens in those places. On with the show.
1) VMWare
Most obvious choice. Our team uses this for incident response at the Firm. Whats nice about this solution is that you don’t have to worry about the same controls that you would a normal computer (AV, firewall, patches). I have gold images of unpatched versions of Windows XP/2003/8 Beta and Ubuntu ready to go. Whether I intentionally or unintentionally infect myself, this becomes irrelevant when I roll back to my original image after I’m done.
2) Sandboxie
I’ll admit it… I am a computer nerd with an embarrassingly slow computer at home (I have only since upgraded it to 768MB of memory). For this reason, VMware isn’t a great option as you’ll effectively be needing the resources of 2 systems. Sandboxie allows you to spawn every application imaginable inside itself and prohibits it from modifying the critical parts of your computer. After you close out, you can back out your changes and everything will be as it was before you started. I use this for Web and Usenet browsing.
3) CCLeaner/SDelete
This doesn’t really go along with theme here, but I do think its of honorable mention. Occasionally you’ll find yourself performing activities online that would make you seem less than honest in a court of law should your computer ever be seized (heres lookin’ at you, RIAA). Although this doesn’t apply to me per se, I am paranoid to the point where I have both of these scheduled to run on a monthly basis. CCLeaner is set to wipe all cookies, browsing histories, and temporary files. Once that is complete, Sdelete has the abililty to scan through all my harddrives and zero out any unallocated space so that any deleted data could not be forensically recovered. Oh yea, and I also have a magnet built into my doorframe to degauss any HD’s that pass underneath…
WMI Scripting
Adam Arceneaux | 19. March, 2009
We recently faced the problem of auditing Microsoft patch compliance on systems that do not have File and Print Sharing installed. Most enterprise patch compliance tools, including Shavlik and MBSA, use F/P sharing to connect and query the registry for installed patches. An interesting way to get around this problem is WMI scripting. Using WMI, you can connect to a remote machine, provide alternate credentials, and pull system information, all without having access to F/P sharing. Additionally, all Windows hosts can natively run WMI scripts so it doesn’t require the installation of any additional libraries or frameworks.
I put together a number of scripts using WMI to pull different types of system information. The first difficulty came in feeding the target computer and credentials to the script. The following script excerpt prompts the user for the host and authentication information.
‘Get target host and credentials
Wscript.StdOut.Write “Please enter target host:”
strComputer = Wscript.StdIn.ReadLine
Wscript.StdOut.Write “Please enter your user name:”
strUser = Wscript.StdIn.ReadLine
Set objPassword = CreateObject(“ScriptPW.Password”)
Wscript.StdOut.Write “Please enter your password:”
strPassword = objPassword.GetPassword()
The second sticking point was that we needed to use local authentication for the hosts. As such, we needed a way to dynamically assign the hostname as the domain for the credentials. Alternatively, if you are using domain credentials, you would simply replace “strComputer” with the domain name.
strDomain = strComputer
After that, it’s just a matter of choosing what values to pull from the registry. I developed three scripts to pull three different sets of information that I thought would be helpful.
The first script addresses the original reason for the WMI scripts, monitoring patch compliance. It pulls a list of installed MS patches from the host, including the KB number. The full script can be found here.
The second script was an extension of patch and vulnerability monitoring and pulls a list of all applications installed on the host, including version numbers. This information can be useful if a new vulnerability is discovered for a non-MS application that may be installed in your environment and you do not have a robust application patching procedure. The full script can be found here.
The final script I created was designed to be used for incident response. It pulls a list of all services on a host, including the service name and full path of the executable. This provides a quick and free way to pull services from a machine that may be infected. The full script can be found here.
All of the scripts output the results to a tab-separated text file that incorporates the script name and target hostname into the filename for easy identification.
There are many other applications that WMI scripting can be used for, but I will not cover them all here. If you have any questions or want additional detail or examples, leave a comment.
Valentine’s Day and Botnets
Deron Grzetich | 18. February, 2009
Social engineering is never going to go away. So, as Valentine’s Day has passed there is little doubt that the Waledac botnet just got a little bit bigger. I was passed a link that made it through into a user’s personal email account (read:hotmail) that contained a link to a greeting card from someone they didn’t know. At least our awareness campaign at work seems to be working since the user did not open the link and simply forwarded it on to us.
Want to connect your system to the Waledac botnet? Follow this link: http://kgiooc.greatvalentinepoems.com/?code=1ded8ca8edba09d6a295130 and download postcard.exe (WARNING: This is the actual malware exe, and if you run it you are infecting your system). Just for fun, try to upload a copy to www.virustotal.com and see how many AV engines find this as a Trojan…was yours in the list? If not, consider using NOD32…for some reason you never hear about them but they have a very high catch rate for malware. I’m not endorsing the product, but it does seem to work well for ~$40.
More info about the Trojan and the botnet here: http://www.eset.com/threat-center/blog/?p=536
System Hardening – Unnecessary Service Disabling for Dummies
Art Chaisiriwatanasai | 26. January, 2009
When performing a system based audit (or if you are the one being audited), you will no doubt run into the recommendation of disabling unnecessary Windows services. The problem with this is that there are many services that are started by default, and the Windows built-in explanations don’t make it any easier.
Usually, this audit recommendation is taken with a grain of salt and only the glaringly bad services will actually be disabled (telnet, snmp, etc.). I ran into this site the other day that will help clear all this up:
http://www.devotedgeek.com/the-ultimate-guide-to-tweaking-useless-windows-xp-services/
This site lists each default service one at a time, and explains scenarios for their use. Very helpful for the technical auditor without the high-functioning rainman type autism to remember these types of things.
Search Engine Optimization Injection
Art Chaisiriwatanasai | 24. January, 2009
Heres a really interesting quasi-cross-site scripting/phishing attack that uses Google rankings to propagate malicious links.
http://garwarner.blogspot.com/2008/12/more-than-1-million-ways-to-infect-your.html
To summarize:
1) An attacker finds legitimate (and hopefully popular) websites that are vulnerable to external site redirection via URL injection.
2) Using a script, this link is posted around the intarwebs such that it is picked up many, many times by Google crawler bots. Since it piggy backs off the popularity of the host’s domain name, its rankings will be vaulted to one of the top search results.
3) User clicks on this link after performing a Google search and is redirected to the infected site.
4) = Profit ??
One common web app I know that is susceptible to URL redirection is Outlook Web Access when running on Exchange 2003. If you append a site to the end of the main login page, you will be redirected to that site once you try logging in (ie. https://owa.good-site.com/exchweb/bin/auth/owalogon.asp?url=http://bad-site.com) Not sure how you would craft this into an earth shattering attack unless people are actively searching for a company’s exchange server, but I’m just throwing it out there as an example.
Interview with an Adware Author
Austin Diener | 13. January, 2009
The folks over at philosecurity.org posted a revealing interview with Matt Knox, an ex-adware designer/creator for Direct Revenue. Check out the following snippet:
So we’ve progressed now from having just a Registry key entry, to having an executable, to having a randomly-named executable, to having an executable which is shuffled around a little bit on each machine, to one that’s encrypted– really more just obfuscated– to an executable that doesn’t even run as an executable. It runs merely as a series of threads.
Rethinking Vulnerability Scoring
Art Chaisiriwatanasai | 1. December, 2008
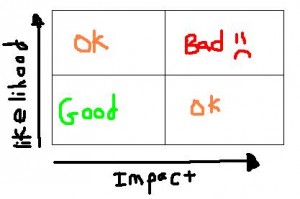
When a vulnerability is identified within an organization, how is its risk measured? One popular method is to assess likelihood vs impact. Numbers are assigned to both factors and plotted on a heat matrix (shown below).
In case you haven’t already guessed, any vulnerabilities that are plotted in the first quadrant are rated as high severity, which are given first priority for remediation. Quadrants two and four are ranked as medium risk, while the third are low and last in the queue. There are a couple flaws with this method. First, it is very, very difficult for a person to consistently assign ratings to vulnerabilities in relation to each other. So many environmental variables exist that could cause the rating to fluctuate that you either end up over-or-under-thinking its value. Instead of a scatter plot of dots, you’d almost need a bubble surrounding each point indicating error margin. Although not entirely arbitrary, its probably the next best thing to it. Secondly, since only two factors are involved, likelihood and impact are boiled up into very high level thought processes instead of calculated, consistent valuations. As the graph shows, there are only three possible risk rankings: high, medium, and low. This leads the assessor to become complacent and risk averse, by placing most vulnerabilities in the “medium” severity quadrants.
The solution? Enter CERT’s Vulnerability Response Decision Assistance (VRDA) Framework. They have published a proposal for further refining the process of vulnerability prioritization, as well as possible courses of action. Each vulnerability is given a value through a pre-defined set of criteria, or as CERT calls them, “facts”. To summarize:
Vulnerability Facts
- Security Product – Does the vulnerability affect a security product (Yes/No)
- Network Infrastructure Product – Does the vulnerability affect a network infrastructure product? (Yes/No)
- Multiple Vendors – Does the vulnerability affect multiple vendors? (Yes/No)
- Impact 1 – What is the general level of impact of the vulnerability on a system? (Low, Low-Medium, Medium-High, High)
- Impact 2 – What are the levels of impact for confidentiality, integrity, and
availability of the vulnerability on a system? (Low, Low-Medium, Medium-High,
High) - Access Required – What access is required by an attacker to be able to exploit the
vulnerability? (Routed, Non-routed, Local, Physical) - Authentication – What level of authentication is required by an attacker to be able
to exploit the vulnerability? (None, Limited, Standard, Privileged) - Actions Required – What actions by non-attackers are required for an attacker to
exploit the vulnerability? (None, Simple, Complex) - Technical Difficulty – What degree of technical difficulty does an attacker face in
order to exploit the vulnerability? (Low, Low-Medium, Medium-High, High)
World Facts
- Public Attention – What amount of public attention is the vulnerability receiving?
(None, Low, Low-Medium, Medium-High, High)
- Quality of Public Information – What is the quality of public information available
about the vulnerability? (Unacceptable, Acceptable, High)
- Exploit Activity – What level of exploit or attack activity exists? (None, Exploit
exists, Low activity, High activity).
- Report Source – What person or group reported the vulnerability?
Constituency Facts
- Population – What is the population of vulnerable systems within the
constituency? (None, Low, Low-Medium, Medium-High, High)
- Population Importance – How important are the vulnerable systems within the
constituency? (Low, Low-Medium, Medium-High, High)
Although some of these facts I feel are irrelevant, this improves upon original methods greatly. The most obvious is that there are not only more criteria to evaluate, but they are consistent and specific. Also, you will notice that none of these have the standard low-medium-high ratings. The article explains that this was purposeful, as to “reduce the tendency of analysts to select the median ‘safe’ value”.
The article also presents a decision tree for actions items after you have performed your scoring. Although I won’t go into great lengths here, I think it is a novel concept and something that should be developed further. Every organization will need to sit down and plan their own, as models will vary by industry and size.